WordPress has become an extremely popular content management system that powers over a third of all websites. However, this widespread adoption also makes it an enticing target for cyber attackers seeking to capitalize on vulnerabilities. Although the WordPress core codebase undergoes regular security audits and patching, many vulnerabilities can be traced back to third-party plugins that extend the functionality of WordPress installations. These plugins, often developed by smaller teams or individual developers, can inadvertently introduce security holes that expose websites to potential compromise.
One critical type of vulnerability often found in WordPress plugins is privilege escalation flaws. These vulnerabilities enable lower-privileged users to gain higher access privileges, allowing them to carry out unauthorized actions on the website.
Privilege escalation bugs can have severe consequences, potentially allowing attackers to control a website completely. Let’s explore how these flaws commonly arise and what developers can do to prevent them.
Common Causes of Privilege Escalation Flaws
Improper Access Checks
Many privilege escalation issues stem from plugins failing to properly validate a user’s capabilities before allowing sensitive operations. Developers need to remember to implement robust access controls, or they could risk inadvertently opening the door to unauthorized users.
Incorrect User Role Mapping
WordPress has specific user roles like Administrator, Editor, Author, etc. Plugins need to carefully map their custom capabilities to these roles. Mistakes in this mapping process can unintentionally grant additional privileges to lower roles.
Lack of Data Validation
Plugins that accept user input without properly sanitizing and validating data are susceptible to attacks that could enable privilege escalation. Malicious users may be able to modify parameters or inject code that circumvents access restrictions.
Case Study
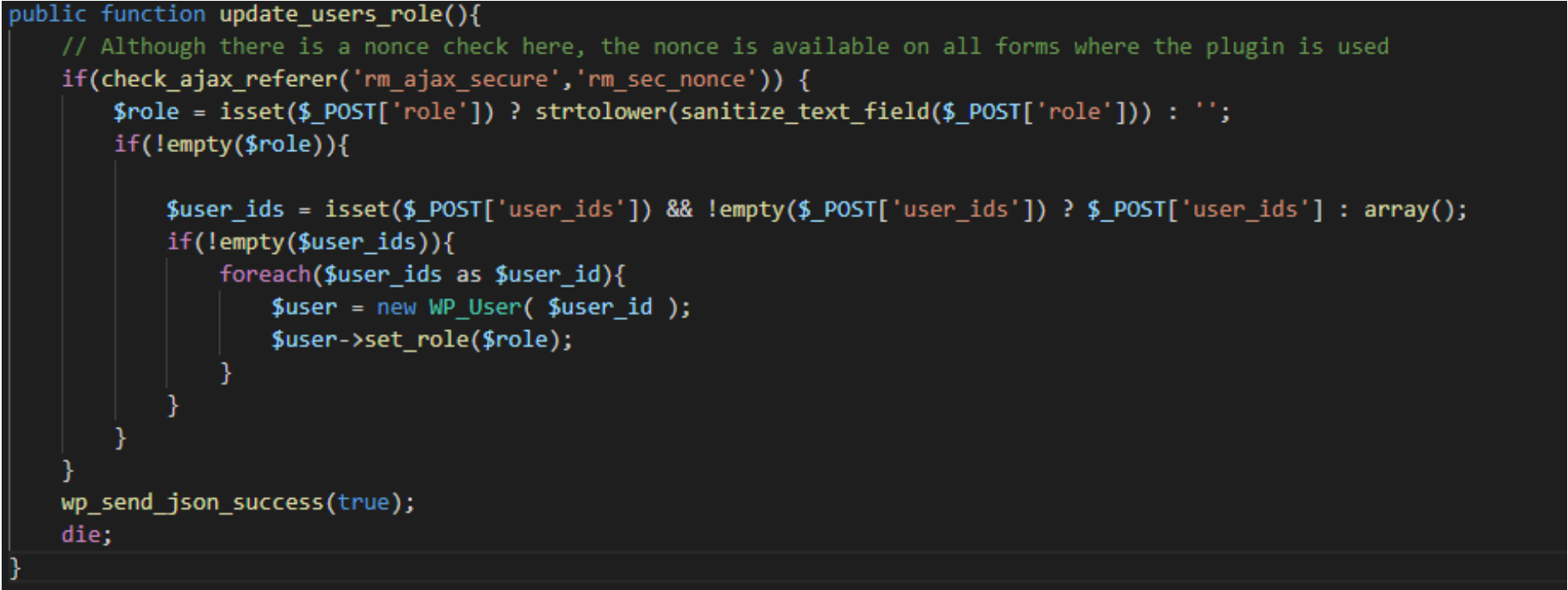
Earlier this month, a critical severity privilege escalation vulnerability was discovered in RegistrationMagic <=5.3.0.0 , a plugin with over 10,000 active installations that offers multiple features such as custom registration forms and analytics tools.
The vulnerability exists in the update_users_role() function which updates the user role. However, the function fails to check the capabilities of the user calling the AJAX function, which allows the user to set their own administrator user role.
Mitigating the Risk
Follow the Principle of Least Privilege
Give users the minimum set of capabilities required for their role/tasks. Avoid excessive permissions that may inadvertently lead to privilege escalation if exploited.
Implement Robust Access Controls
Validate the current user’s role and capabilities whenever executing sensitive operations. WordPress nonces and permissions checks should be applied rigorously.
Use Sanitization/Escaping Functions
Leverage built-in WordPress data sanitization, validation, and escaping functions consistently to prevent unauthorized data passing.
Conduct Security Reviews
Have experienced developers review code for appropriate access controls, user mapping, and data validation before deploying to a live environment.
Continuous Testing
Include extensive test cases in your plugin development process to identify and remediate potential privilege escalation issues before release.
With its widespread usage, WordPress has become an attractive target for attackers, and privilege escalation vulnerabilities in plugins represent a common attack vector. However, by adhering to security best practices and vigilantly avoiding common mistakes, plugin developers can fortify their products against these critical flaws, effectively safeguarding websites and users from potential compromise.
At Summit, we understand the importance of securing web applications like WordPress sites and plugins. Our experienced security team offers comprehensive web application testing services to identify and help mitigate vulnerabilities before they can be exploited. Whether you need an in-depth WordPress plugin analysis or a complete website assessment, Summit has the expertise to protect your online assets from cyber threats.


