The adage “trust but verify” is a principle that emphasizes the importance of verifying the trustworthiness of a person, system, or piece of information, even if you have a reason to trust it.
In the cybersecurity world, there are many occasions in which you need to trust something to perform a given task, like requiring a piece of software to perform automated backups across an organization. Without verifying the integrity and authenticity of the software, how can you know that what you are using is safe?
Do you have a process for vetting a third-party vendor? What about validating a file’s integrity? How would you determine if a file has been tampered with? Do you or your company make exceptions for downloading software without checksums or signatures? If you are not sure, you may be introducing additional risk into your organization.
After all, the process of validating the integrity and authenticity of data can be both time-consuming and confusing. Taking the time to search for the software developer’s public key, certify the key, find the correct signature file, create a checksum of the downloaded file, and then compare the checksum to the one posted by the developer, is a lot of effort, especially when you are in a rush to push code out quickly.
The risks of avoiding this process, however, far outweigh the frustration of validating software’s authenticity and integrity.
The Dangers of Unverified Software
In 2016, the Linux Mint project fell victim to an attacker who compromised their website and replaced their official operating system’s .iso file with a version that included a backdoor. While the Linux Mint team acted quickly to shut down the operation, some users had already downloaded and installed the compromised version.
This is a clear example of why a careful validation process is crucial. Users who had the developer’s public keys before the attack would have been able to determine that the .iso files did not come from the Linux Mint developers and that something had gone wrong.
Overlooking these checks can lead to vulnerabilities that might otherwise be easily prevented with just a bit of extra diligence. To protect against these kinds of threats, tools like GPG and processes like checksums offer a reliable way to validate the software before you use it.
GPG and SHA Sums
When it comes to validating the legitimacy of files, two common methods are using GPG (GNU Privacy Guard) for signature verification and SHA (Secure Hash Algorithm) sums for checksum validation. Both techniques help ensure the integrity and authenticity of files, and I recommend using both when they are made available by the developer(s).
How GPG Works to Verify Authenticity of Data
At a high level, GPG is a key-based tool used for signing, encrypting, and validating files. It relies on public and private key cryptography, which can be thought of as a lock and key.
Only one person has the (private) key, but everyone has your lock (public key). You can give your locks (public key) to anybody so they can use your locks to protect things they want only you to open (files, messages, etc.). When you receive an item with your lock on it, you can unlock it using your key.
How Checksums Work to Verify Data Integrity
Checking the file’s integrity can be achieved by generating a checksum of the downloaded file, and comparing it against the one provided by the developer (usually found on their website).
Checksums exist to help users validate that the file they have downloaded is not corrupt or has not been altered in any way while in transit.
Using GPG and SHA Sums to Validate Files
In practice, there are a few tools that make the process of verifying the authenticity of data much easier.
On Windows, there is Gpg4win, a front-end for the command-line tool GPG, which includes a suite of tools like Kleopatra for key management and GPGOL for email encryption.
For Linux, Kleopatra serves as a powerful GUI tool that simplifies key management and file verification, using GPG.
On Mac, GPG Tools offers similar functionality, including GPG Suite, which features GPG Keychain for managing keys and GPG Mail for encrypted communication.
Each of these tools provides a GUI to interface with GPG and offers a more user-friendly way of navigating through the processes of importing public keys, creating key pairs, and verifying file signatures.
A Real-World Example Using GPG & Kleopatra
To demonstrate this in an example, I’ll guide you through the process of using Kleopatra and GPG to verify the authenticity of a downloaded file; in this case, we will be downloading GnuPG.
Assuming you have Kleopatra and GPG installed, the first step is to open Kleopatra and create your first certificate. This certificate will be used to locally validate all new certificates you import from other sources. To do this, click ‘File’ and click ‘New OpenPGP Key Pair’. From there, you will be prompted to enter some information, as seen below:
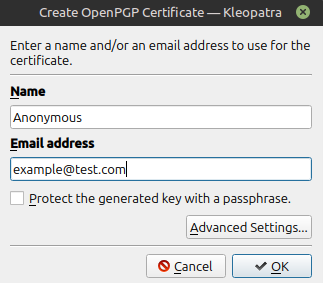
I would recommend protecting the key with a passphrase and then clicking ‘OK’ to save the certificate.
Now, since we want to download GnuPG from the GnuPG website, we will first need to obtain and certify the developer’s keys in Kleopatra. On the GnuPG website, there exists a section in which you can download all of the developer’s keys, as seen below:
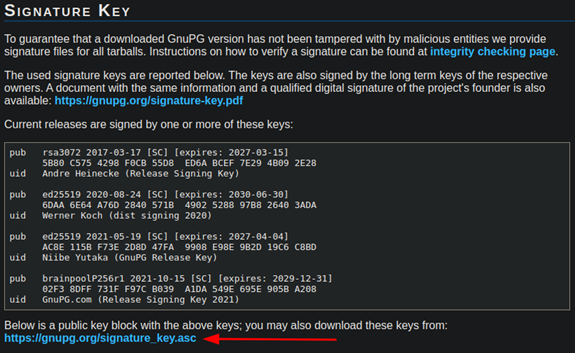
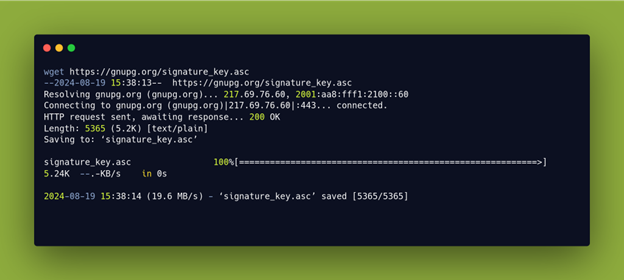
We can download these with the command-line utility, wget, and store these developer keys in a local file on our device.
After downloading these keys, we can use GPG to import them.
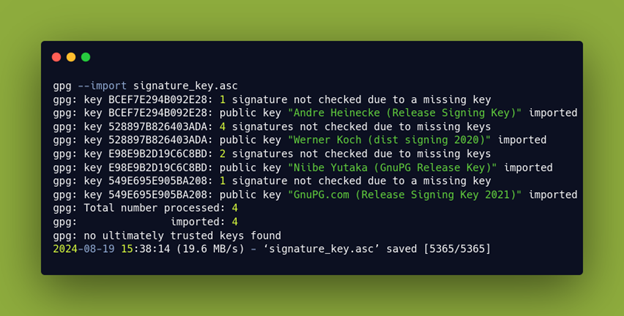
Each of the keys will now appear in Kleopatra.
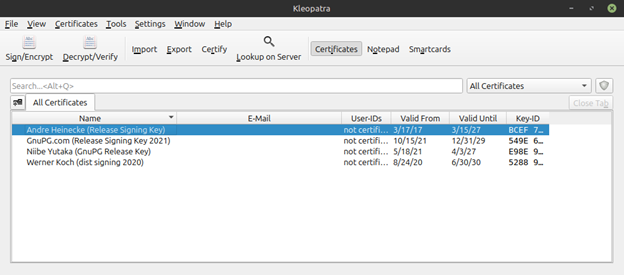
We now need to certify each of them using the certificate we created in the first step. You can achieve this by right-clicking each of the developers ’ names and selecting ‘certify’.
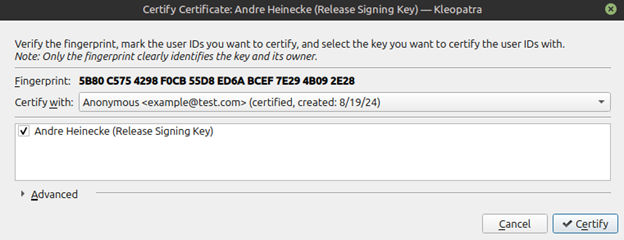
To make sure these are the keys we intend to certify, we need to compare the fingerprint of each key to those shown on the website. In this case, Andre’s fingerprint matches what was provided on the website, so we know we are ok to certify this key.
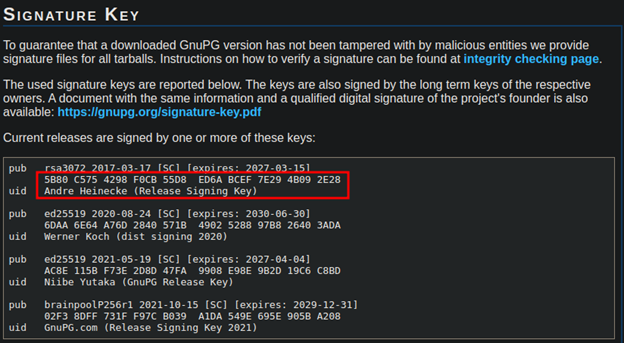
Once we have certified each of the developer’s keys, we can now download our software and its associated signature. GnuPG offers links to the software and its signature on the download page, as seen below.
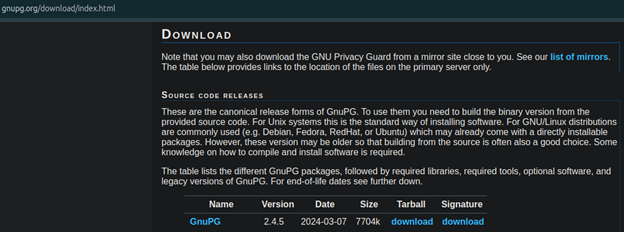
We will download both the software and its signature file using wget.
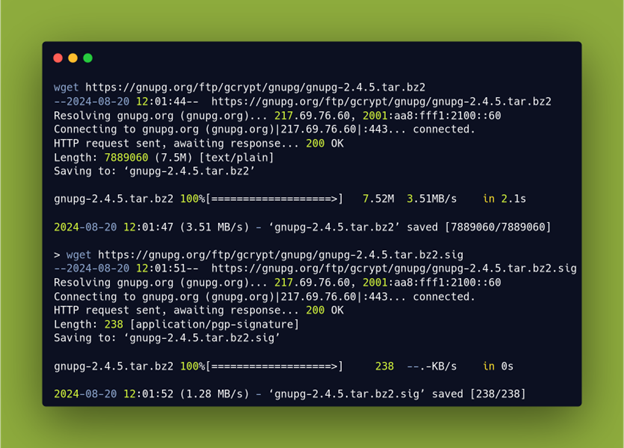
We can now use Kleopatra to confirm that the downloaded software is authentic. To do this, we will click ‘File’ and then select ‘Decrypt/Verify’. From there, select the GnuPG tarball and its signature file ending in ‘.sig’. After selecting ‘open’ in your file manager, Kleopatra will confirm that the signature of the downloaded file is valid, as seen below:
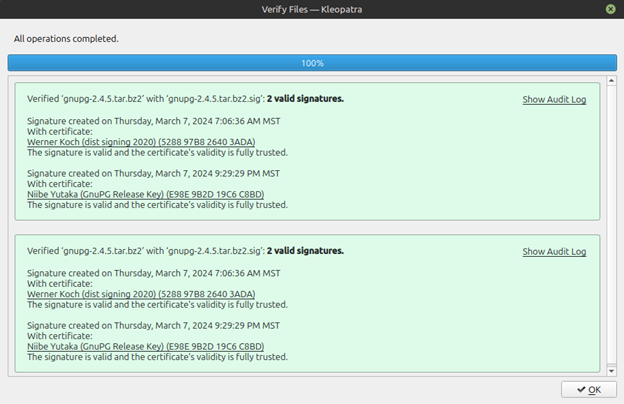
Upon completing this process, we can now confirm that we have the correct developer keys and the correct software downloaded. Next, we want to make sure the file was not altered during our initial download, by validating its checksum.
Validating GnuPG’s Checksum
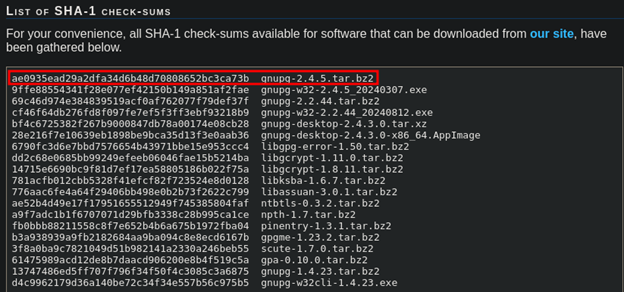
GnuPG provides all of the checksums for each version of GnuPG on their website. Since we downloaded the latest version of GnuPG, 2.4.5, we want to compare our downloaded file’s checksum with the checksum provided by the developers, as seen below:
We can then create a checksum of our own local file using sha1sum and compare it to what is displayed on the website.
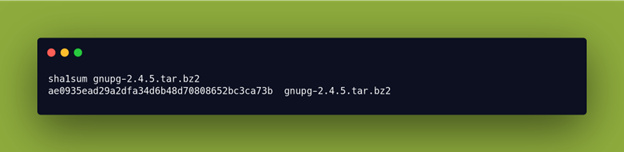
This checksum from our downloaded file is the same as what is displayed on the website, so we have now confirmed that we have downloaded the intended file.
Why This Matters
Validating the authenticity and integrity of files is often an involved process, but it is a necessary one. Companies must ensure their developers have the time and resources to perform these security checks, as skipping them can lead to significant risks. Neglecting this step can lead to severe consequences, such as unknowingly incorporating malicious libraries into your codebase or deploying compromised software to your customers, which could ultimately jeopardize the security of your entire operation.
To mitigate these risks, consider implementing a process that outlines the steps needed to verify and establish a trusted list of developers, companies, and software and create a policy that maintains and updates the list as time goes on. At Summit Security Group, we specialize in helping companies navigate these decisions, offering guidance on best practices that protect both your business and your clients from potential threats. For personalized assistance, contact us to learn how we can support your security needs.


