The Summit Team recently uncovered multiple web-based vulnerabilities in a manufacturing system during a recent penetration test of a large food distribution company. This post details how our team discovered the vulnerabilities and some ways you could better secure your Operational Technology (OT) environment.
The Summit Team was engaged by a large food distribution company to perform an authorized network penetration test. During the test, we observed that a Mettler Toledo Safeline X3310 X-Ray** machine appeared to lack sufficient security controls.
During testing, we were able to remotely control the machine via VNC without providing any credentials which gave us plenty of insight as to how the machine worked, what sort of data it stores, and the types of programs it could execute. Our scope of work did not include tampering with the machine’s settings, so we moved on to identify other areas of interest.
We later found security issues in a simple-looking webserver hosted on port 80.The web server refreshed every few seconds with a new X-Ray image and lacked much functionality. Apart from the system’s lack of encryption on the web server, our curiosity was piqued when we discovered that the web server exposed the “web.config” file and full server path during 404 errors — both typically understood as not meeting best practices. These factors suggested the web server was likely vulnerable to other forms of exploitation.
We decided to poke around the interface a bit more to see if there was any sort of additional functionality. After some time however, it seemed as though the webserver’s only use was in reporting the status of the X-Ray. We then included some simple Cross-Site Scripting (XSS) payloads in the URL to see how the web server would respond, and just like that, the payload fired.
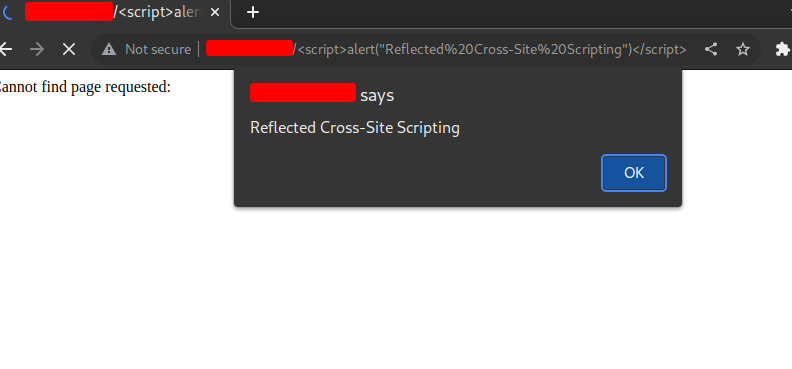
This occurred because the web application did not sanitize user input (in this case malicious JavaScript payloads) in a manner that prevents an attacker from rendering JavaScript in a victim’s browser.
For some additional proof-of-concept, we included some HTML in the URL, which was also displayed by the browser. Here, you can see us insert a “malicious” link on the web page:
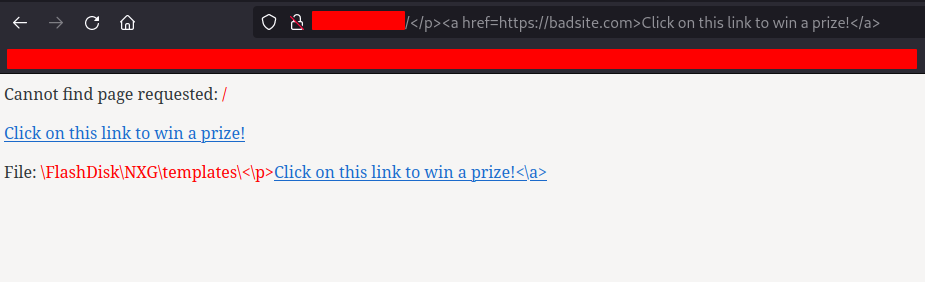
Both the XSS and HTMLi vulnerabilities appear to affect NXG version 19.05 on the MT Safeline X-Ray X3310 system.
The Summit Team is not currently aware of a patch for these issues. Summit notified Mettler Toledo of the issues, asked to confer with a member of their team regarding vulnerabilities with their products, and also submitted two CVE requests to MITRE. MITRE reserved the CVEs as 2023-25199 and 2023-25200. Mettler Toledo has not responded as of the date of this posting. The details of our disclosure attempts are discussed below under Responsible Disclosure Timeline. Summit will update this posting when a patch is available or if we learn more from Mettler Toledo.
The primary method to reduce vulnerabilities in an OT environment is to perform thorough security testing before, during, and after deploying the system(s). When vulnerabilities are present, a patch can solve the issues when available. Until a patch is released, the best way to fix these issues is to restrict access to the system to only necessary users and to implement server-side protections such as a Web Application Firewall (WAF) to deny users the ability to inject JavaScript or HTML into the URL.
Thanks for reading and stay safe out there!
Responsible Disclosure Timeline:
- February 3rd, 2023 – Identify and report issues to Mettler Toledo and MITRE.
- February 6th, 2023 – MITRE reserved CVE-2023-25199 and CVE-2023-25200.
- February 6th, 2023 – Reach out to Mettler Toledo for a second time.
- February 13th, 2023 – Reach out to Mettler Toledo for a third time.
- February 28th, 2023 – Reach out to Mettler Toledo for a fourth time.
- February 28th, 2023 – Reach out to Mettler Toledo via LinkedIn.
- March 8th, 2023 – Reach out to Mettler Toledo a fifth time.
- March 21st, 2023 – Reach out to Mettler Toledo a sixth time.
- March 14th, 2024 – Publish Findings
**Summit has no affiliation or relationship with Mettler Toledo


